Business Technology for Windows 10 Device Login
Every project is different. Time and time again when working on client projects, as I dig deep into different technologies, I find myself having to jump over endless technical hurdles in order to meet customers’ needs. My exhaustive research inevitably leads me to discover new workarounds that allow me to not only successfully complete my current assignments but could apply to future projects as well. I hope that sharing some of what I have learned, will not only help prevent future headaches, but will also help you to build your toolbox when working on tough projects of your own.
In this blog, I will cover how to implement Windows Hello for Business (WHFB) in your organization. As a quick reminder, WHFB is a technology that allows you to use multiple unlock factors to login to a Windows 10 device in lieu of traditional set of user credentials. Here at Withum, we have been assisting our customers to satisfy 2FA-like requirements and others as they go through their compliance effort towards NIST, CMMI and other regulation frameworks.
As you look at WHFB capabilities, you will find that there are different types of architecture that can be rolled out. In this post, I will focus on the Hybrid Azure AD Joined Key Trust Deployment. This setup will leverage your existing Active Directory/Azure Active (AD/AAD) Hybrid setup using Azure AD Connect and “Password Sync/Pass-Through Authentication” as well as your Windows 10 machines which are hybrid Azure AD Joined. If you are Active Directory Federation Services (ADFS) with your AD/AAD deployment, you would be able to use the Hybrid Azure AD Joined Certificate Trust Deployment. While the certificate architecture requires more server footprint, that deployment does provide Remote Desktop 2FA capabilities whereas the Key Trust deployment does not.
The Hybrid Azure AD Joined Key Trust Deployment has the following pre-requisites:
- Windows 10 version 1511 or later (or version 1903 for self-service PIN Reset)
- Windows Server 2008 R2 Domain/Forest Functional level or later
- Windows Server 2016 or later DCs
- PKI Infrastructure: Windows Server 2012 or later Certificate Authority
- Azure MFA
- Azure AD
- Azure AD Connect
Once the infrastructure is in place, you can use GPO policies to customize your WHFB deployment. You will want to make sure to add the latest Administrative Template (.admx) for Windows 10 and add them to your SYSVOL folder (\\contoso.com\SYSVOL\contoso.com\policies\PolicyDefinitions) on your Domain Controller so you can access the latest GPOs.
Below are the key GPOs you should be considering (located under GPO -> Computer Configuration -> Administrative Templates -> System -> Windows Hello for Business)
- Use PIN Recovery
- Enabled
- Self-Service PIN reset for users who forgot their PIN
- Enabled
The Microsoft PIN Reset service only works with Enterprise Edition for Windows 10, version 1709 to 1809. The feature works with Enterprise Edition and Pro edition with Windows 10, version 1903 and newer.
- Use biometrics
- Enabled to allow compatible laptops/webcams to act as an Unlock factor
- Configure device unlock factors
- Factor Types:
- First unlock factor
- PIN
- Fingerprint
- Facial Recognition
- Trusted Signal: Phone proximity via Bluetooth, Network location
- Second unlock factor
- PIN
- Trusted Signal: Phone proximity via Bluetooth, Network location
- First unlock factor
- Factor Types:
For trusted signals used as unlock factors, we configured on-premises networks and Bluetooth:
<rule schemaVersion=”1.0″>
<signal type=”ipConfig”>
<ipv4Prefix>10.10.10.0/24</ipv4Prefix>
</signal>
</rule>,
<rule schemaVersion=”1.0″>
<signal type=”bluetooth” scenario=”Authentication” classOfDevice=”512″ rssiMin=”-10″ rssiMaxDelta=”-10″/>
</rule>
In case of multiple IP ranges for all your corporate offices, you should be looking at adding your ipv4Prefix with a larger subnet mask if possible to include multiple subnets at once, or else you may run into character limitations when adding your xml to the GPO.
The user experience ends up following the patterns below:
- While in the Office (Already Satisfying one unlock factor: Network Location Trusted Signal):
- PIN; or
- Fingerprint (if available on the laptop); or
- Facial recognition (if compatible webcam available on the laptop)
- While on an external/home network
- PIN and have your mobile phone paired to your laptop via Bluetooth; or
- Fingerprint and PIN; or
- Facial Recognition and PIN; or
- Fingerprint and have your mobile phone paired to your laptop via Bluetooth; or
- Facial recognition and have your mobile phone paired to your laptop via Bluetooth
- Use Windows Hello for Business
- Enabled
- Configure dynamic lock factors
- Enabled
- As long as users pair their phones to their Windows 10 laptop via Bluetooth, the machine will be locked automatically when the paired phone is no longer in close proximity to the computer.
- Enabled
- PIN Complexity configuration
- GPO -> Computer Configuration -> Administrative Templates -> PIN Complexity
Once the hybrid Azure AD Joined machine receives the GPO and the machine is restarted, the user will be prompted for WHFB Enrollment. The creation of the PIN will be mandatory whereas biometrics will also be prompted if the laptop camera/fingerprint is compatible with Hello for Business. At this point, the machine can now allow for either WHFB or credentials login.
Finally, there are a couple of options available to remove the credentials login capability. You can hide the password credential provider via GPO: Computer Configuration > Policies > Administrative Templates > Logon -> Enabled -> 60b78e88-ead8-445c-9cfd-0b87f74ea6cd
This will hide the credentials prompt on the Windows login screen; however, it will also prevent you from being able to RDP into other machines. The Key Trust deployment does not support RDP and with this method, the password credential provider will no longer be available when starting a RDP session.
The other option which I recommend is to enable the interactive logon security policy under Computer Configuration > Policies > Windows Settings > Local Policy > Security Options-> Interactive logon: Require Windows Hello for Business or smart card (can also be named Interactive logon Require smart card). This policy will leave the credentials prompt on the Windows login screen but will prevent users from signing in using a password and they will get the following message when attempting to do so:
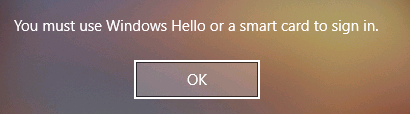
Note that you should wait until all your corporate machines are 1) hybrid Azure AD Joined and 2) enrolled in WHFB before configuring interactive logon security policy since it will block enrollment as soon as you turn it on.
Currently available, but in its preview mode, is the introduction of the FID02 Security Keys which will act as another Unlock Factor. These keys which can connect via USB or NFC (no OTP Tokens) to the machine will also be able to provide users the ability to sign-in when their devices are offline.
As Microsoft works on transitioning firms to a password-less experience, we can expect more and more options to come out. Users will greatly benefit from an approach that is both more secure and more convenient when logging in.
Digital and Technology Transformation



