As 2020 thankfully stumbled to a close, the most substantial and potentially costly U.S. cyberattack campaign to ever strike the nation’s targets (both government and private industry) was being detected. The attack was operating covertly within network monitoring utilities for approximately nine months prior to its detection.
This article is the first of two-part series concerning the U.S. cyber attack, popularly referred to as the “SolarWinds breach” and the “2020 U.S. federal government data breach.” This part will focus on the attack itself, its’ indicators for concerned SolarWinds users seeking to determine their exposure, and the best recommendations of what to do should concerns arise that your organization or firm is amongst the thousands directly impacted.
What Happened And Why Is It Such A “Big Deal”?
At the time of this article’s writing, information is still emerging rapidly regarding the number of affected users and the magnitude of the attacks, as measured by the cost of total damage or lost/compromised data. The general consensus is that a remote access tool (RAT [1]) trojan was inserted into the SolarWinds Orion network monitoring utility by the hacking group Cozy Bear [2] (threat designation nomenclature: APT29) at some point in time earlier than October 2019. The attacker’s means of breach into the SolarWinds network is still under intense investigation and is critically important to corrective measures since this breach served as the de facto origin event for this attack as a whole. The attackers surreptitiously inserted the RAT into, at last count, 18,000+ end-user systems running SolarWinds Orion as their network manager by way of the regular Orion March 2020 Update. The RAT was hidden in this update and was able to covertly hitch a ride into the wide-open world of the large Orion user base.
This user base was particularly sensitive because it counted amongst its number most of the U.S. Government’s Departmental and Agency critical networks, including the Department of State, Homeland Security (DHS), U.S. Treasury, Defense (DOD), Energy (DOE), Commerce, the National Institutes of Health (NIH), and the National Nuclear Security Administration, to name just a few of the largest and most sensitive. Add to this the fact that the private corporate networks affected include Microsoft (more on this impact in Part 2 of this article), FireEye, Boeing, AstraZeneca, and thousands more – the scope, scale, and success of this attack is believed to be unprecedented historically.
- Microsoft identifies 40+ victims; most are in the United States
- Microsoft quarantines trojanized apps
- Hackers accessed Microsoft source code
- Malicious Code Overlaps with Turla [3] malware
- U.S. Government officials formally blamed the hack on Russia
- Hacking Group APT29 aka Cozy Bear is suspected of being involved.
- A Second Hacking group targets SolarWinds systems
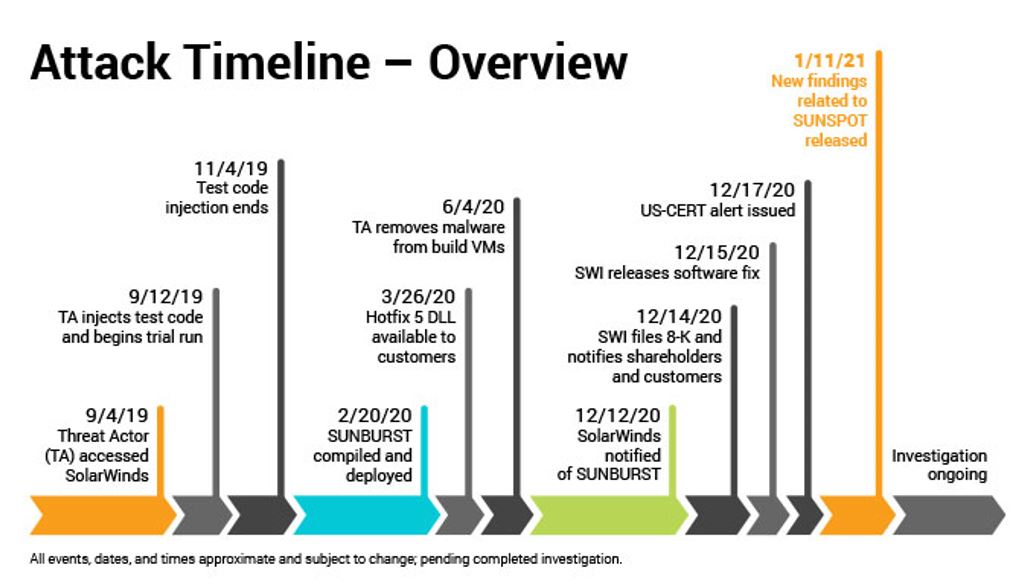
Graphic courtesy of ChannelE2E
Have I Been Breached?
A primary (yet counterintuitive) consideration must be that, given the large number of potentially exposed networks (18,000+), the likelihood of a given user being actively breached by the attackers is relatively low in the near term. Even with nine months of undetected opportunity period for attack and exploitation, only a fraction of the affected userbase will have been breached with subsequent network exploitation and/or data exfiltration. However, if your organization knowingly or unknowingly has these risks, it is only a matter of time before the risks are exercised and your organization is impacted. Similar to a roulette wheel, eventually, your number will come up. Except, it will not be in your organization’s favor.
Withum’s Cyber and Information Security Team recommends taking a conservative (and intelligent) approach towards this incident, meaning this: If your organization/firm is a SolarWinds Orion user, assume you are, at minimum, at an elevated risk of breach and implement corrective response actions immediately. There are a few indicators to look for, which may suggest a significantly higher likelihood of an active breach. Volexity has published a detailed blog post describing these indicators, which may be accessed here.
Two quick and easy indicators visible via log review are:
- Examine your systems to see if you were or are running Orion Platform versions 2019.4 HF 5,2020.2 with no hotfix installed or with 2020.2 HF 1.
- Look at your organization’s current and historic DNS queries to see if there have been DNS queries to hostnames on the domain avsvmcloud[.]com (from Volexity blog post / 16 December 2020)
What Should I Do?
If any indicators are present, incident response measures should be taken immediately (if they haven’t begun already precautionarily). It is also recommended to review Emergency Directive 21-01, issued by the government Cybersecurity and Infrastructure Security Agency (CISA) on 13 December 2020.
A rapid yet informed and disciplined response is essential in potential security breach scenarios. From Incident Response support to expert advice and consultation through full Active Breach Response services, our Cyber team is standing by to assist with preliminary risk assessments and scanning to determine if your organization is at risk and/or in an incident response capacity. However, avoiding an incident and impact via an assessment / scanning of the environment is advised. In some cases, our team has identified organizations which were unaware that their environment was at risk and being impacted. A proactive approach is always less costly than dealing with a material impact. Review the full breadth of our cybersecurity services here and contact us by phone (avail. 24/7) at (800) 470-0988.
Stay tuned for part two of this article, which will focus on the threat entity believed to be behind an attack of this scope, what this event’s historical implications may be for information and network/IT security practices and the potentially far-ranging impact to the security of Microsoft software products which are ubiquitous in global commerce.
[1] Remote Access Trojan (RAT) is a type of malware that is very dangerous; it allows a backdoor into a victim’s computer and network while maintaining unauthorized administrative level controls over the computer and data, remote access connectivity and has the capability to execute additional code, including malicious code, on the victim’s system. A RAT also conducts covert surveillance on a victim’s machine and across the network(s).
[2] Cozy Bear aka APT29 (Advanced Persistent Threat 29) as classified by the US Federal Government is a Russian hacker group believed to be associated with one or more intelligence agencies of Russia.
[3] Turla (aka Snake aka Uroburos aka Waterbug aka Venomous Bear aka Krypton) is a malware strand that has been in operation since early 2000. Linked to the Russian government, it is one of the most sophisticated pieces of malware and with one of Russia’s most advanced state-sponsored hacking group behind it. The malware and group focus on espionage, targeting government entities and embassies in up to 100 countries. Turla malware succeeds by continuing to evolve itself and by remaining undetected for extended periods of time. The hacker group behind Turla steals antivirus logs to see if its malware is detected in an effort to improve the malware’s stealth and effectiveness.
Contact Us
Withum is here to assess and improve your organization’s cybersecurity habits and hygiene. Contact our Cyber and Information Security Services Team today to get started and feel secure!


